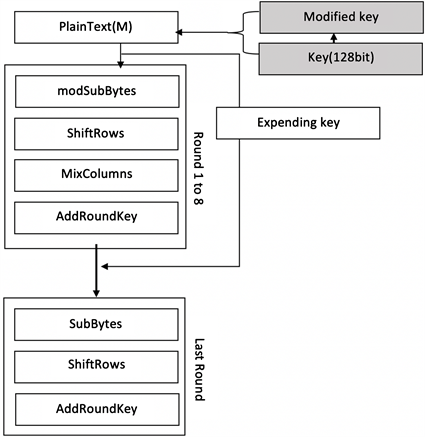
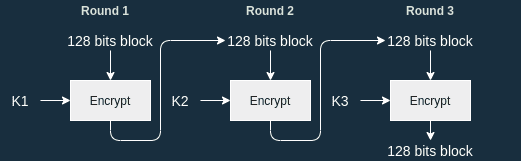
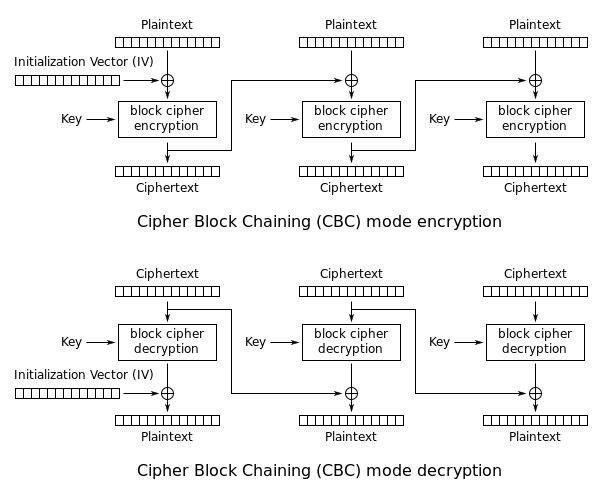
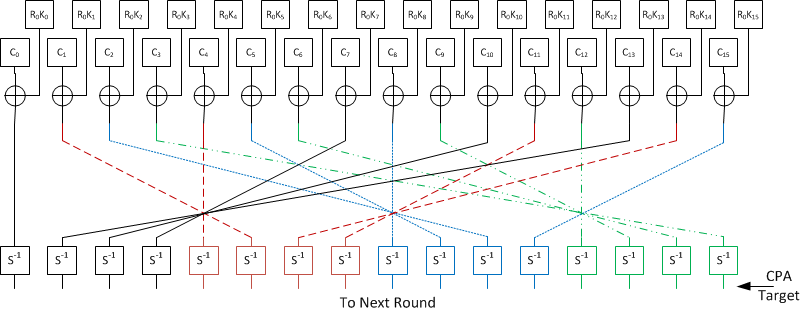
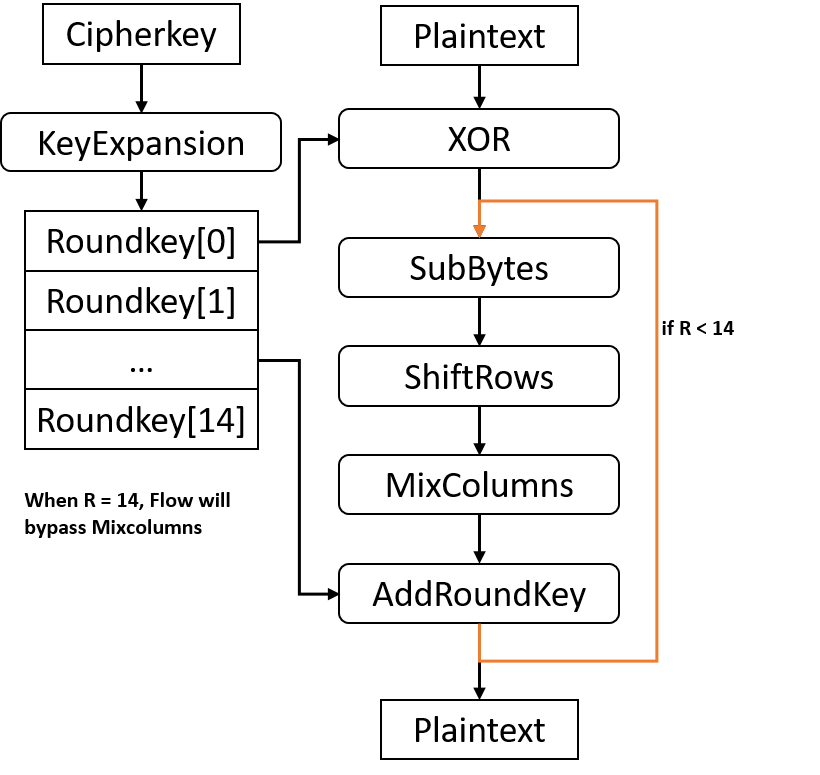
An Introduction to the Advanced Encryption Standard (AES) | by Adrienne Domingus | The Startup | Medium
53 Gbps Native GF(2 Composite-Field AES-Encrypt/Decrypt Accelerator for Content-Protection in 45 nm High-Performance Microproces

AES Encryption 256 Bit. The encryption standard to rule them… | by Cory Maklin | Towards Data Science

Encrypt and Decrypt using the Existing AES Which uses Key Addition &... | Download Scientific Diagram
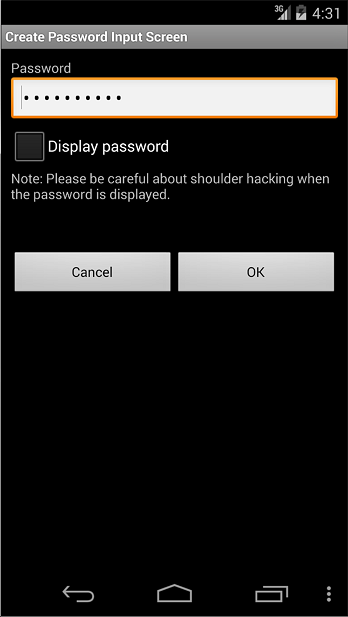
5. How to use Security Functions — Android Application Secure Design/Secure Coding Guidebook 2022-01-17 documentation
aes-128-cbc encryption with 32 byte key and 16 byte IV failing with "Invalid Key length" · Issue #27622 · nodejs/node · GitHub